
Key Findings from the White Paper:
1. SOC Tools: Are They Enough?
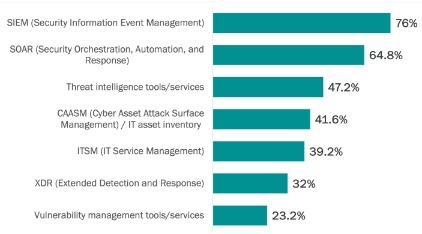
- 76% of SOCs rely on SIEMs, 64.8% use SOAR, and 47.2% leverage threat intelligence tools. But despite the widespread use of these tools, SOCs are struggling to manage alert volumes and address incidents quickly enough.
2. The Growing Alert Volume Problem
- 97.6% of organizations report an increase in security alerts each year.
- Despite efforts, alert backlogs continue to grow, leaving organizations at risk of missing critical threats.
3. Current SOC Tools Are Losing Efficacy
- The time to address alerts has dropped, but it’s still not enough. SOCs aim for a 55% reduction in time to begin working on alerts and a 50.7% decrease in time to close incidents. Achieving these goals will require rethinking SOC processes and toolsets.
4. The AI Threat: Escalating Complexity
- 82.4% of organizations believe AI-driven cyberattacks will have the most significant impact on SOCs in the next 24 months. With increasingly sophisticated and evasive attack methods, traditional tools are struggling to keep pace.
5. The Reactive SOC: A Bottleneck
- Over 65% of SOCs spend more time in reactive mode than being proactive. Moving towards a proactive security posture is critical to reducing alert fatigue and improving efficiency.
What’s Next for SOCs?
This white paper examines how SOCs can better equip themselves to handle the growing threat landscape, the evolving role of AI in cyberattacks, and how adopting advanced technologies like XDR (Extended Detection and Response) can dramatically improve security posture and reduce operational inefficiencies.
Actionable Insights:
- Modernize your tools: Leverage next-gen solutions like XDR, SOAR, and AI-powered threat intelligence to cut down investigation times and improve alert correlation.
- Optimize SOC workflows: Implement automation, prioritization, and incident orchestration to reduce alert fatigue and backlogs.
- Shift towards proactive security: Invest in hardening defenses, proactive threat intelligence, and employee training to prevent attacks before they occur.
This article is posted at ostermanresearch.com

Please fill out the form to access the content





